5 Steps to Implement Zero Trust Architecture in your OT Environment Zero-trust architecture is a critical component of
Five Steps to Implement Zero Trust Architecture in your OT Environment
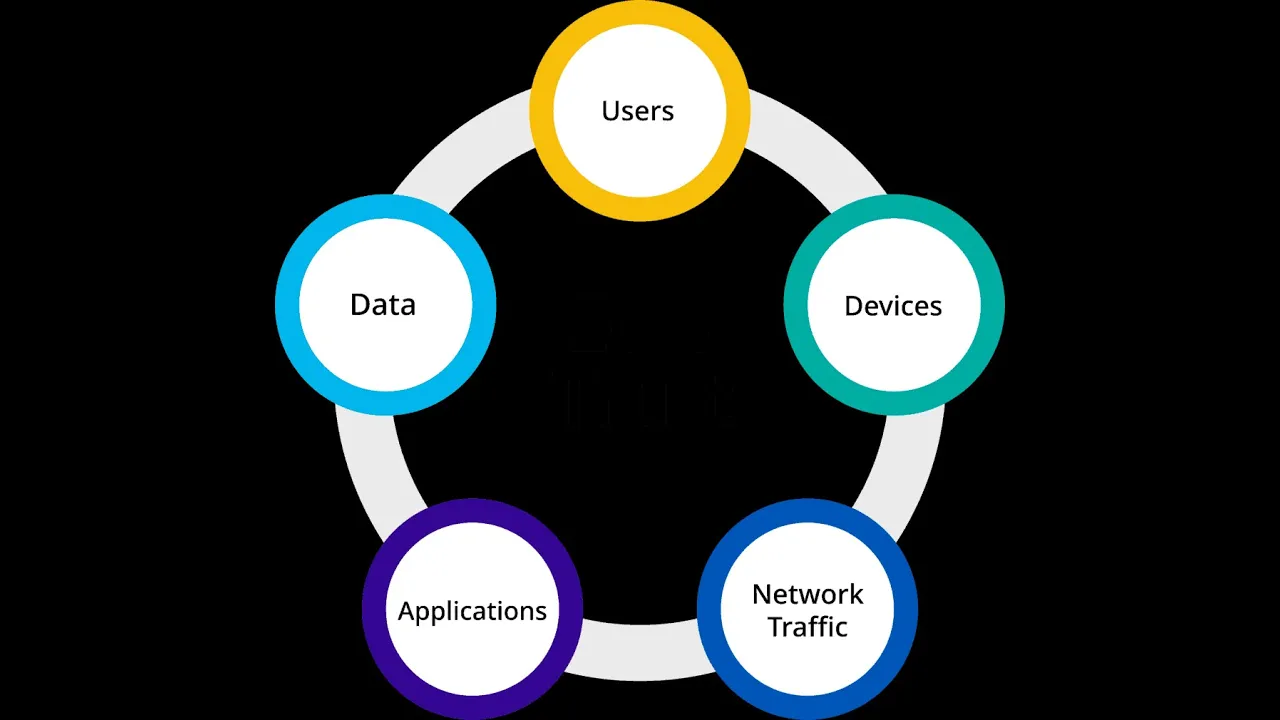

5 Steps to Implement Zero Trust Architecture in your OT Environment Zero-trust architecture is a critical component of