5 Steps to Implement Zero Trust Architecture in your OT Environment
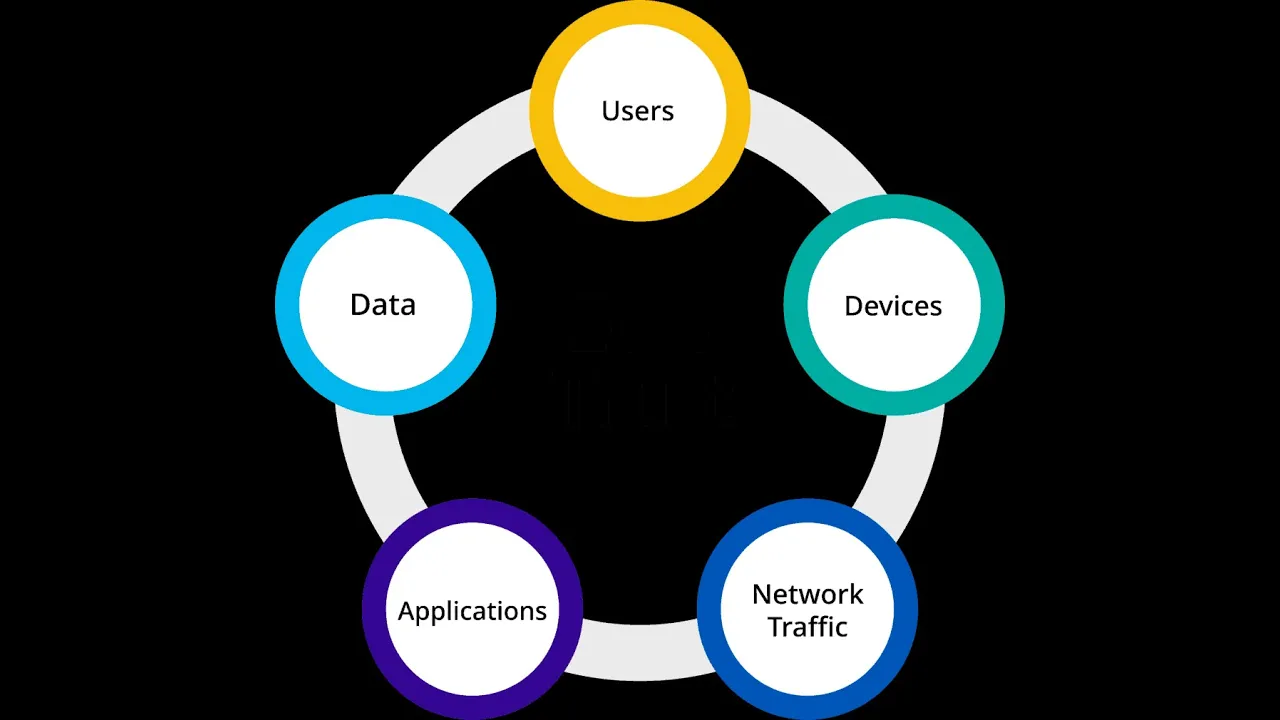
Zero-trust architecture is a critical component of operational technology security. Here are five steps to implement zero-trust architecture in your OT environment.
✅ Identify and classify all assets, including devices, data, and applications.
✅ Conduct a thorough risk assessment to identify potential vulnerabilities and threats.
✅ Define and enforce security policies for access and authentication, ensuring that only authorized users and devices can access the network.
✅ Implement security controls such as firewalls, intrusion detection and prevention, and segmentation. ✅ Continuously monitor and evaluate the network for any anomalies or potential threats. With these five steps, you can implement zero-trust architecture in your OT environment and ensure the safety and security of your operations.